Top 5 identity & access management (IAM) tools for 2024
We’re going to discuss the Top 5 Identity and Access Management (IAM) tools of 2024. An IAM tool is a framework or software solution that helps manage developers' and users' identities and control user access to resources within an organization. Identity verification, directory services, authorization mechanisms, and logging capabilities form the backbone of robust security frameworks. IAM tools ensure precise identity verification through advanced authentication methods, manage user information and organizational structures via comprehensive directory services, and enforce precise access controls through refined authorization policies. Additionally, they maintain detailed logs of all IAM-related activities, providing an essential audit trail for security monitoring and compliance.
In 2024, the landscape of Identity and Access Management (IAM) tools is evolving rapidly, blending cutting-edge security features with user-centric designs and seamless integration capabilities. These tools' core are advanced authentication methods, comprehensive directory services, precise authorization policies, and detailed activity logs—elements crucial for safeguarding digital identities and managing access within an organization's IT infrastructure.
For developers implementing Cerbos, choosing the right IAM tool is more than just a strategic decision; it's about enhancing security frameworks to manage and control access efficiently. Many of our users are often in the process of selecting an IAM solution that complements Cerbos, seeking advice on integrating Cerbos with their existing or prospective IAM systems. Here's what we generally tell them: Cerbos is designed to work hand in hand with IAM tools, adding an extra layer of fine-grained, context-aware access control that bolsters your organization's security and operational efficiency. Whether you're looking to manage access to tens of thousands of servers, the synergy between Cerbos and a robust IAM tool can significantly strengthen your defense against cyber threats and streamline access management processes. Integrating Cerbos with your IAM solution optimizes your security posture and future-proofs your access management strategy against digital complexities. This strategic combination ensures that your business is equipped for secure, efficient, and compliant operations, ready to face the challenges and opportunities of the emerging integrated world.
IAM tools are essential for enhancing security, streamlining access management processes, and ensuring compliance in organizations.
IAM tools ask three critical security questions:
- Who is allowed access? (Identity) Each user’s identity is verified before granting them access to an account.
- Which account should have access to what? (Access) Once the verified user is granted access, the system ensures each user has the correct privileges within the system for their needs.
- How are they using that access? (Access) The IAM system then monitors user activities to identify any access issues or detect potential misuse of privileges by the user or by bad actors.
Selection Criteria
Choosing the perfect Identity and Access Management (IAM) tool is quite the task, especially when you've got a bunch of specific needs and scenarios to consider. Let's break it down.
For professionals in the finance or healthcare sectors, where regulations are tighter than a drum, it's all about compliance and auditing. You've got to have an IAM tool that's up to snuff with GDPR, HIPAA, or SOX. This means robust audit trails, top-notch reporting, and the ability to set access controls precisely. And let's remember to beef up security with things like multi-factor authentication, biometrics, and risk-based authentication to keep all that sensitive data under lock and key.
If you're dealing with an ocean of users, scalability is your best friend. Your IAM tool must handle the crowds without breaking a sweat, ensuring smooth sailing during those peak times. To keep things running smoothly, self-service features are a godsend, letting users handle their passwords and access dramas, which is a win-win for everyone.
On the flip side, if you're a smaller outfit with big security needs, it's all about getting granular with access controls and not skimping on the security features. Think adaptive authentication and continuous monitoring to keep those sneaky threats at bay.
Life's a breeze for those managing a global or scattered team with Single Sign-On (SSO) and federated identity management. These are lifesavers for keeping user experiences smooth across the board, no matter where your team is or what they're accessing. And when it comes to juggling identities across different domains and platforms, having a tool that can keep up is non-negotiable.
Hybrid IT setups, with their mix of on-premises and cloud environments, need an IAM tool to bridge the gap seamlessly, ensuring access policies are consistent no matter where your resources live. For cloud enthusiasts, having cloud-native features is like having the right tool for the job, ensuring everything integrates just right.
Lastly, for those navigating the complex web of user roles and hierarchies, an IAM tool that's flexible with role-based access control can make life much easier. For an extra layer of finesse, attribute-based access control lets you make decisions based on a rich tapestry of user, resource, and environmental attributes.
After carefully assessing several important aspects, we selected the best IAM tools for 2024.
1. IBM Security Identity and Access Assurance
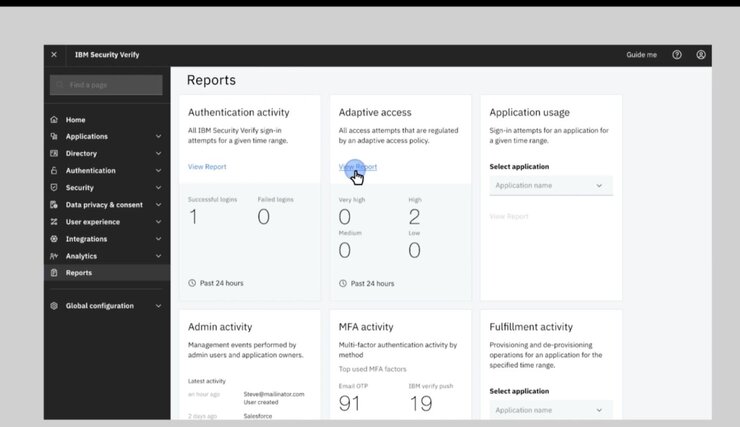
IBM Security Identity and Access Assurance provides integrated identity and access management across cloud and on-premises environments. It facilitates compliance reporting and threat intelligence by actively monitoring user activities and securing sensitive data. The tool is designed to enhance user experience by operating seamlessly within organizational workflows, and it offers robust features for protecting privileged accounts, including advanced password security.
However, the comprehensive nature of the solution can lead to complexities in deployment and management, which may pose challenges for organizations without a dedicated IT security team. Additionally, while the tool aims to provide a holistic IAM solution through its expanded capabilities in identity governance and privileged access management, this breadth can increase the learning curve and resource requirements for effective utilization.
Pros:
- Comprehensive Coverage: Combines user provisioning, role management, and compliance controls in one package, offering a holistic approach to IAM.
- Advanced Analytics: Leverages AI and machine learning for real-time threat detection and adaptive access decisions, enhancing security posture.
- Strong Integration: Seamlessly integrates with a wide range of enterprise applications and systems, facilitating a unified IAM framework.
Cons:
- Complexity: The comprehensive nature of the solution might introduce complexity in deployment and management, particularly for organizations without a dedicated IT security team.
- Cost: As a robust and feature-rich solution, the total ownership cost might be higher than simpler IAM tools, potentially making it less accessible for smaller organizations.
IBM Security Identity and Access Assurance with Cerbos
IBM's IAM suite offers robust identity governance and administration. By integrating Cerbos, organizations can leverage its policy-as-code model to define fine-grained access controls, further enhancing IBM's capabilities. Cerbos' low-latency checks and stateless operation mean it scales effortlessly with IBM's suite, ensuring consistent policy enforcement across different services without impacting performance.
# Conceptual Integration Steps:
User Authentication with IBM Security Identity and Access Assurance:
The user logs in through an interface that uses IBM Security Identity and Access Assurance.
IBM's tool authenticates the user and establishes their session.
Retrieve User Identity and Context:
After authentication, the application retrieves the user's identity and any relevant context or roles assigned by IBM's IAM tool. This might involve API calls to IBM IAM or extracting information from a session token.
Set Up Cerbos Authorization Check:
The application uses the Cerbos client to prepare for an authorization check, defining the Principal with the user's identity and roles, and the Resource with details about the object the user is trying to access.
Perform Authorization Check with Cerbos:
The application sends a request to Cerbos to determine if the authenticated user is authorized to perform the desired action on the resource, based on the policies defined in Cerbos.
Conceptual Python Code Example:
from cerbos.sdk.client import CerbosClient
from cerbos.sdk.model import Principal, Resource, CheckResourceRequest
# This function is conceptual and represents retrieving user identity and roles from IBM's IAM tool post-authentication
def get_user_identity_and_roles():
# Implement the logic to retrieve the authenticated user's identity and roles
# This might involve API calls to IBM IAM or decoding a session token
user_identity = "john_doe" # Example user identity
roles = ["manager"] # Example roles assigned to the user
return user_identity, roles
# Initialize the Cerbos client
cerbos_client = CerbosClient("http://localhost:3592")
# Retrieve the authenticated user's identity and roles from IBM's IAM tool
user_identity, user_roles = get_user_identity_and_roles()
# Define the principal for Cerbos with the user's identity and roles
principal = Principal(user_identity, roles=user_roles)
# Define the resource and action the user wants to perform
resource = Resource("document", "doc123", attr={"confidential": True})
action = "read" # The action the user wants to perform
# Create a request for Cerbos to check if the user is authorized to perform the action
request = CheckResourceRequest(principal, resource, action=action)
# Use Cerbos to check the authorization
result = cerbos_client.check_resource(request)
# Decision based on Cerbos' response
if result.is_allowed:
print("Access granted by Cerbos.")
else:
print("Access denied by Cerbos.")2. Microsoft Azure Active Directory
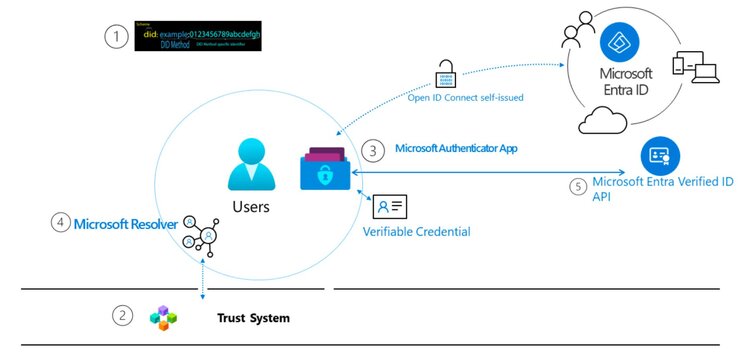
Microsoft Azure Active Directory, rebranded as Microsoft Entra ID, is a cloud-based identity and access management service provided by Microsoft. It offers single sign-on (SSO) and multi-factor authentication (MFA) capabilities, facilitating secure and convenient access to cloud applications.
The service integrates well with Microsoft's ecosystem and various third-party applications, making it a suitable option for enterprises looking for a unified IAM solution. Its cloud-native architecture is designed for high availability and resilience, aiming to maintain service continuity even during disruptions.
However, Azure AD's reliance on other Microsoft products may limit its appeal for organizations with diverse IT environments not centered around Microsoft technologies. Additionally, it lacks support for traditional Active Directory features such as organizational units and group policy objects, which could pose challenges for organizations dependent on these for user and device management.
Pros:
- Azure AD operates as a cloud service, eliminating the need for local infrastructure and reducing associated costs and maintenance efforts.
- It supports Multi-factor Authentication (MFA) and Single Sign-On (SSO), enhancing security and user convenience.
- Azure AD efficiently manages user and computer access and includes mobile device management (MDM) capabilities.
- Being part of the Microsoft stack, it integrates seamlessly with other Microsoft products, providing a cohesive environment for users.
Cons:
- The utility of Azure AD is maximized when used in conjunction with other Microsoft products, which might limit its appeal to users outside the Microsoft ecosystem.
- Unlike traditional Active Directory, Azure AD doesn't support organizational units and group policy objects, which could be a limitation for organizations that rely on these features for managing users and devices.
- The structure of Azure AD is flat compared to traditional hierarchical models, which might affect the organization and management of large, complex networks.
- The absence of domain controllers and domain services in Azure AD might require adjustments in how identity services are managed and authenticated within an organization.
In contrast to traditional Active Directory, which focuses on local authentication and managing user access to on-premises resources, Azure AD is a cloud-based identity and access management service. This distinction makes Azure AD more suitable for managing access to a wide range of internal and external services in a cloud environment.
Microsoft Azure Active Directory (Entra ID) and Cerbos
Incorporating Cerbos with Entra ID into Microsoft systems allows for implementing complex access control scenarios beyond Azure's built-in role-based access control (RBAC) system. This integration enables dynamic authorization policies that respond to changing business requirements, and all are managed through Cerbos' intuitive policy language and GitOps workflow.
# Prerequisites:
- Azure AD Setup: Ensure your Azure AD (Microsoft Entra) environment is configured with users and groups.
- Cerbos Instance: Have a Cerbos instance running and accessible from your application, with policies defined for your resources and actions.
- Python Libraries: Make sure the necessary Python libraries are installed. You might need msal for Microsoft Authentication Library and cerbos-sdk for Cerbos. Install them using pip if you haven't already:
pip install msal cerbos-sdk
Python Code Example:
import msal
from cerbos.sdk.client import CerbosClient
from cerbos.sdk.model import Principal, Resource, CheckResourceRequest
# Azure AD app registration details
CLIENT_ID = 'your-azure-ad-client-id'
TENANT_ID = 'your-azure-ad-tenant-id'
CLIENT_SECRET = 'your-azure-ad-client-secret'
AUTHORITY = f'https://login.microsoftonline.com/{TENANT_ID}'
SCOPES = ['https://graph.microsoft.com/.default']
# User details
USER_EMAIL = 'user@example.com'
# Initialize MSAL Confidential Client
confidential_client = msal.ConfidentialClientApplication(
CLIENT_ID, authority=AUTHORITY,
client_credential=CLIENT_SECRET
)
# Acquire Token
token_response = confidential_client.acquire_token_for_client(scopes=SCOPES)
# Call Microsoft Graph API to get user's group memberships
graph_api_url = 'https://graph.microsoft.com/v1.0/users/{}/memberOf'.format(USER_EMAIL)
graph_response = confidential_client.acquire_token_on_behalf_of(
token_response['access_token'], scopes=SCOPES, user_assertion=USER_EMAIL
)
groups = [group['displayName'] for group in graph_response.get('value', []) if group['@odata.type'] == '#microsoft.graph.group']
# Initialize the Cerbos client
cerbos_client = CerbosClient("http://localhost:3592")
# Define the user (Principal) for Cerbos with groups from Azure AD as roles
principal = Principal(USER_EMAIL, roles=groups)
# Define the resource and action the user wants to perform
resource = Resource("document", "doc123", attr={"confidentiality": "high"})
action = "read" # The action the user wants to perform on the resource
# Create a request for Cerbos to check if the user has permission to perform the action
request = CheckResourceRequest(principal, resource, action=action)
# Use Cerbos to check the permission
result = cerbos_client.check_resource(request)
# Decision based on Cerbos' response
if result.is_allowed:
print("Access granted by Cerbos.")
else:
print("Access denied by Cerbos.")
# Notes:
- Azure AD Configuration: Replace 'your-azure-ad-client-id', 'your-azure-ad-tenant-id', and 'your-azure-ad-client-secret' with your actual Azure AD app registration details.
- Token Acquisition: This example uses client credentials flow for simplicity. Depending on your app's requirements, you may need to use a different authentication flow.
- Graph API Call: The Graph API call here is simplified and may need adjustments based on your Azure AD setup. Specifically, the memberOf endpoint might require pagination handling for users with many group memberships.
- Cerbos Policies: Ensure your Cerbos instance has policies defined that correspond to the resources and actions used in this example, considering the group memberships from Azure AD as roles.Ping Identity
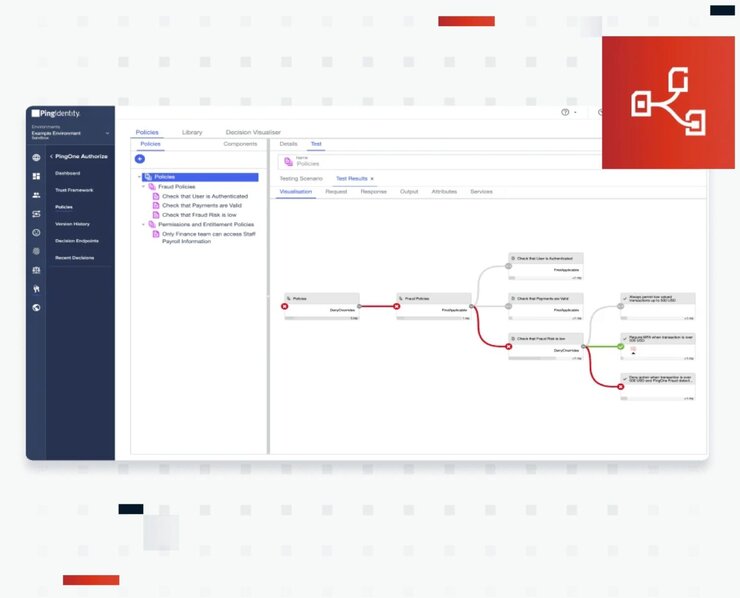
Ping Identity offers IAM solutions that address modern security challenges and embrace new security models such as Zero Trust and passwordless authentication. Their products are designed to facilitate secure and seamless digital interactions, supporting a wide range of single sign-on (SSO) requirements for various applications, devices, and user scenarios. This includes providing secure access from both mobile devices and traditional desktop environments.
The solutions are scalable and include features like automated user provisioning and compatibility with standard identity protocols, which can simplify user management processes. Ping Identity is also moving towards eliminating reliance on traditional password-based security, advocating for more secure and user-friendly authentication methods.
However, the transition to advanced security models like Zero Trust and passwordless systems may require significant changes to existing IT infrastructure and processes, which could pose implementation challenges for some organizations. Additionally, the breadth of features and the shift towards newer authentication methods may necessitate a learning curve for IT teams, potentially impacting the initial adoption phase.
Pros:
- The platform is known for its reliable and efficient login process, which includes a third layer of authentication, enhancing security.
- It offers high ratings for ID Management Single-Sign-On (SSO) and Multi-Factor Authentication (MFA), indicating strong performance in these critical areas.
- The solution is adaptable to a range of IT environments, designed for both on-premises and cloud deployments, providing centralized control to balance security and convenience.
Cons:
- Some users have mentioned the need for improvement in session management, suggesting that the platform could offer more control over session timeout settings to enhance the user experience.
- The interface aesthetics and occasional delays in the authentication process were noted as areas that could be enhanced.
- While the platform's focus on security is commendable, it's been pointed out that pairing with older phones and authorizing new devices can sometimes be challenging, potentially impacting user experience.
Overall, Ping Identity's solutions appear well-regarded in the industry, especially for organizations looking for robust and flexible identity management systems. The feedback suggests that while there are areas for improvement, the platform's strengths in authentication, user management, and adaptability make it a strong contender in the IAM space.
Ping Identity Enhanced by Cerbos
Integrating Cerbos with Ping Identity can extend its capabilities by adding more nuanced, context-aware authorization policies. This allows for the enforcement of granular access controls based on user attributes, environmental conditions, and resource characteristics, making the overall IAM framework more adaptable and secure.
# Prerequisites:
- Ping Identity Setup: Ensure your Ping Identity environment is configured with users and roles.
- Cerbos Instance: Have a Cerbos instance running and accessible from your application, with appropriate policies for your resources and actions.
- Python Libraries: Make sure you have installed necessary libraries for interacting with Ping Identity and Cerbos. This might include libraries like requests for API calls and cerbos-sdk for Cerbos. If not already installed, you can add them using pip:
pip install requests cerbos-sdk
Python Code Example:
import requests
from cerbos.sdk.client import CerbosClient
from cerbos.sdk.model import Principal, Resource, CheckResourceRequest
# Ping Identity details
PING_IDENTITY_API_ENDPOINT = 'https://your-ping-identity-server/api'
PING_IDENTITY_API_KEY = 'your-ping-identity-api-key'
USER_ID = 'user@example.com'
# Function to get user roles from Ping Identity
def get_user_roles_from_ping(user_id):
headers = {'Authorization': f'Bearer {PING_IDENTITY_API_KEY}'}
response = requests.get(f'{PING_IDENTITY_API_ENDPOINT}/users/{user_id}/roles', headers=headers)
if response.status_code == 200:
return [role['name'] for role in response.json()['roles']]
else:
return []
# Get user roles
user_roles = get_user_roles_from_ping(USER_ID)
# Initialize the Cerbos client
cerbos_client = CerbosClient("http://localhost:3592")
# Define the user (Principal) for Cerbos with roles obtained from Ping Identity
principal = Principal(USER_ID, roles=user_roles)
# Define the resource and action the user wants to perform
resource = Resource("file", "file123", attr={"sensitivity": "high"})
action = "access" # The action the user wants to perform on the resource
# Create a request for Cerbos to check if the user has permission to perform the action
request = CheckResourceRequest(principal, resource, action=action)
# Use Cerbos to check the permission
result = cerbos_client.check_resource(request)
# Decision based on Cerbos' response
if result.is_allowed:
print("Access granted by Cerbos.")
else:
print("Access denied by Cerbos.")
# Notes:
- Ping Identity Configuration: Replace 'https://your-ping-identity-server/api' and 'your-ping-identity-api-key' with your actual Ping Identity server endpoint and API key.
- User Roles: The get_user_roles_from_ping function is a simplified example of calling the Ping Identity API to get a user's roles. Depending on your Ping Identity setup, you might need to adjust the API endpoint, authentication method, and data parsing.
- Cerbos Policies: Ensure your Cerbos instance has policies defined that correspond to the resources ("file") and actions ("access") used in this example, considering the roles obtained from Ping Identity.Google Cloud IAM
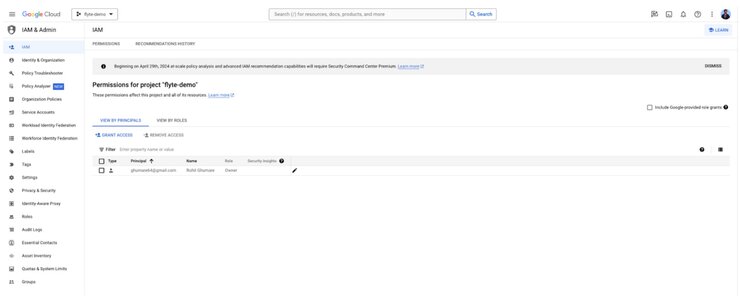
Google Cloud IAM stands as a vital component for managing access within the Google Cloud Platform. Its focus is ensuring that resources are accessible solely to verified and authorized users. Their policies are founded on the “least privilege principle,” allowing for granular control over access based on users' roles. This is achieved through a mix of predefined and customizable roles within a hierarchical resource management framework, ensuring consistent policy application.
Google Cloud IAM enhances security with service accounts for server-to-server interactions within GCP projects. This includes the management of group memberships within projects, allowing for collective access control settings that streamline permissions for users who share common responsibilities. The addition of conditional role bindings in IAM further refines access control, adapting permissions in response to specific scenarios for dynamic, context-aware security measures. These features make Google Cloud IAM an indispensable tool for organizations leveraging GCP, safeguarding digital resources while optimizing operational efficiency.
Pros:
- Principle of Least Privilege: Google Cloud IAM adheres to this principle, ensuring users have only the access they need, which enhances security against unauthorized users.
- Granular Access: It allows for detailed access control to specific GCP services, enabling tailored access needs.
- Integration and Updates: Seamlessly integrates with Google Cloud services and automatically updates with new permissions and features, keeping the system current without manual intervention.
Cons:
- Role Volume: Managing a large number of roles can be challenging, making it difficult to delegate permissions effectively.
- Complex Role Definitions: Some roles might include unrelated permissions, complicating the adherence to the least privilege principle.
- Custom Role Limitations: While custom roles offer tailored access, they can be complex to set up and are limited to the project or organization they were created in, not automatically updating like predefined roles.
These insights underscore Google Cloud IAM's capability to provide secure, granular access control, albeit with challenges in role management and custom role flexibility.
Google Cloud IAM with Cerbos
Google Cloud IAM provides fine-grained access control to resources on Google Cloud. By integrating Cerbos, organizations can define more complex authorization logic that goes beyond predefined roles and permissions. Cerbos' attribute-based access control (ABAC) complements Google Cloud IAM by allowing policies to adapt in real-time to the context of each access request, providing a more flexible and secure environment.
# Prerequisites:
- Google Cloud SDK: Ensure the Google Cloud SDK is installed and configured for your project.
- Cerbos: Have a Cerbos instance running, accessible from your application, and configured with appropriate policies for your resources and actions.
- Python Libraries: Make sure you have google-cloud-iam and cerbos-sdk Python libraries installed. If not, you can install them using pip:
pip install google-cloud-iam cerbos-sdk
Python Code Example:
from google.oauth2 import service_account
from google.cloud import iam
from cerbos.sdk.client import CerbosClient
from cerbos.sdk.model import Principal, Resource, CheckResourceRequest
# Google Cloud IAM setup
credentials = service_account.Credentials.from_service_account_file(
'path/to/your/service-account-file.json'
)
iam_client = iam.IAMClient(credentials=credentials)
# Assume we have a Google Cloud user's email
user_email = "user@example.com"
# Get the IAM policy for a project to determine roles (simplified example)
project_id = "your-google-cloud-project-id"
resource_name = f"projects/{project_id}"
policy = iam_client.get_iam_policy(resource=resource_name)
# Extract roles for the user (this is a simplified approach)
roles = []
for binding in policy.bindings:
if user_email in binding.members:
roles.append(binding.role)
# Initialize the Cerbos client
cerbos_client = CerbosClient("http://localhost:3592")
# Define the user (Principal) for Cerbos with roles extracted from Google Cloud IAM
principal = Principal(user_email, roles=roles)
# Define the resource and action the user wants to perform
resource = Resource("project", project_id, attr={"confidentiality": "high"})
action = "deploy" # The action the user wants to perform on the resource
# Create a request for Cerbos to check if the user has permission to perform the action
request = CheckResourceRequest(principal, resource, action=action)
# Use Cerbos to check the permission
result = cerbos_client.check_resource(request)
# Decision based on Cerbos' response
if result.is_allowed:
print("Access granted by Cerbos.")
else:
print("Access denied by Cerbos.")ManageEngine ADManager Plus
ManageEngine ADManager Plus is an Active Directory management tool designed to facilitate various administrative tasks across AD, Exchange, Teams, Google Workspace, and Microsoft 365. It supports bulk user provisioning and workflow automation, which can help reduce manual efforts and potential errors associated with user management. The tool offers over 150 customizable reports that provide insights into AD activities, which can be beneficial for ensuring compliance with regulations like GDPR and SOX. Features such as Exchange Server mailbox migrations, dynamic distribution group setups, and AD auditing capabilities contribute to its effectiveness in managing complex AD environments.
However, the comprehensive nature of ADManager Plus might introduce complexity, making it overwhelming for new users or small IT teams without dedicated AD specialists. Additionally, while the tool provides extensive customization options, this flexibility can sometimes lead to a steep learning curve, requiring significant time investment to leverage all available features fully.
Pros:
- Enhanced Role-Based Access Compliance: Ensures access permissions are granted according to users' roles within the organization, adhering to the principle of least privilege.
- Streamlined Administrative Tasks: Automates routine tasks such as user provisioning and de-provisioning, password resets, and group management, freeing up valuable time for IT staff.
- Customizable Solutions: Offers flexible customization options to tailor the tool to specific organizational needs and workflows.
- Automation of Repetitive Tasks: Reduces manual intervention by automating repetitive and time-consuming administrative tasks, enhancing efficiency.
- Integration Capabilities: Seamlessly integrates with other tools and applications within the IT ecosystem, providing a unified management solution.
- User-Friendly Interface: Designed with a user-friendly interface that simplifies navigation and operation, making it accessible for administrators with varying levels of expertise.
Cons:
- Limited API Integrations: May lack extensive API support for seamless integration with various HR tools and other enterprise systems.
- Integration with Other Products: Could benefit from more readily available integrations with other products within the ManageEngine suite and beyond for a more cohesive ecosystem.
- Optimization for Mobile Devices: The user interface may not be fully optimized for tablet and mobile use, potentially affecting usability on these devices.
- Feature Efficiency: Certain features, such as bulk email ID creation, might not be as efficient as expected, impacting productivity.
ManageEngine ADManager Plus and Cerbos
ManageEngine ADManager Plus simplifies Active Directory management and reporting. Integrating Cerbos introduces advanced authorization capabilities, allowing for dynamic access control policies based on user roles, attributes, and other contextual information. This integration helps in automating and streamlining access decisions, ensuring that users have the right access at the right time, in line with security and compliance requirements.
# Prerequisites:
- ADManager Plus Setup: Ensure your ADManager Plus environment is configured with users and their roles.
- Cerbos Instance: Have a Cerbos instance running and accessible from your application, with policies defined for your resources and actions.
- Python Libraries: Make sure you have installed necessary libraries for interacting with ADManager Plus (typically via REST API) and Cerbos. You might use requests for API calls and cerbos-sdk for Cerbos. Install them using pip if needed:
pip install requests cerbos-sdk
Python Code Example:
import requests
from cerbos.sdk.client import CerbosClient
from cerbos.sdk.model import Principal, Resource, CheckResourceRequest
# ADManager Plus details
ADMANAGER_PLUS_API_ENDPOINT = 'https://your-admanager-plus-server/api'
ADMANAGER_PLUS_API_KEY = 'your-admanager-plus-api-key'
USER_ID = 'user@example.com'
# Function to get user roles from ADManager Plus
def get_user_roles_from_admanager(user_id):
headers = {'Authorization': f'Bearer {ADMANAGER_PLUS_API_KEY}'}
# Note: Adjust the endpoint and parameters as per ADManager Plus API documentation
response = requests.get(f'{ADMANAGER_PLUS_API_ENDPOINT}/users/{user_id}/roles', headers=headers)
if response.status_code == 200:
# Assuming the response contains a list of roles assigned to the user
return [role['name'] for role in response.json().get('roles', [])]
else:
return []
# Get user roles
user_roles = get_user_roles_from_admanager(USER_ID)
# Initialize the Cerbos client
cerbos_client = CerbosClient("http://localhost:3592")
# Define the user (Principal) for Cerbos with roles obtained from ADManager Plus
principal = Principal(USER_ID, roles=user_roles)
# Define the resource and action the user wants to perform
resource = Resource("document", "doc123", attr={"classification": "confidential"})
action = "view" # The action the user wants to perform on the resource
# Create a request for Cerbos to check if the user has permission to perform the action
request = CheckResourceRequest(principal, resource, action=action)
# Use Cerbos to check the permission
result = cerbos_client.check_resource(request)
# Decision based on Cerbos' response
if result.is_allowed:
print("Access granted by Cerbos.")
else:
print("Access denied by Cerbos.")
# Notes:
- ADManager Plus Configuration: Replace 'https://your-admanager-plus-server/api' and 'your-admanager-plus-api-key' with your actual ADManager Plus server endpoint and API key.
- API Interaction: The get_user_roles_from_admanager function is simplified for illustration. You need to adjust the API endpoint and response parsing based on ADManager Plus's actual API, which may require handling pagination or different response structures.
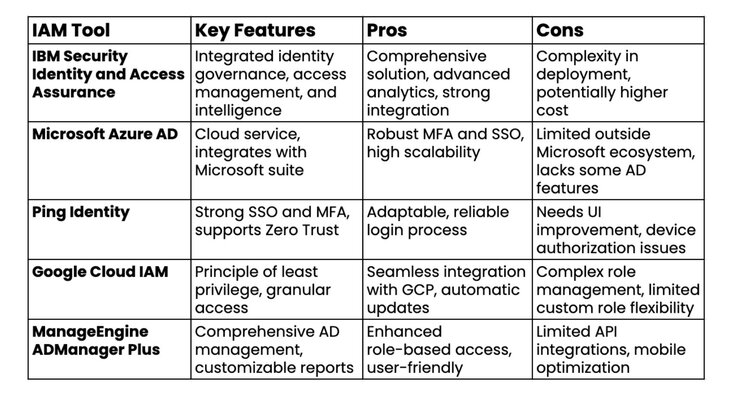
- Cerbos Policies: Ensure your Cerbos instance has policies that correspond to the resources ("document") and actions ("view") used in this example, considering the roles obtained from ADManager Plus.Comparison Table for Reference
Implementation Insights
Choosing an IAM tool is like picking the best lock for your door. You've got to make sure it fits just right. That means checking how it works with what you already have.
It's not a hassle; it's a smart move. This way, the IAM tools you choose will work like a charm with how you do things and keep your place safe.
It's not something to put off. It's a smart step to take care of your digital space. Integrating leading IAM tools into your organization helps enhance security, but it is also a strategic move towards operational excellence and robust defense against unauthorized access and potential data breaches.
A comprehensive security needs assessment tailored to your organization's specific system compatibility is crucial. This analysis ensures that the selected IAM solutions seamlessly mesh with your operational workflows and security requirements, paving the way for a smooth implementation.
Far from being a reason to hesitate, this careful preparation underscores the importance and benefits of adopting an IAM framework. It streamlines the integration process and significantly strengthens your organization's security posture, making implementing IAM solutions an essential and proactive measure for your businesses. It will lead to safeguarding your digital environments effectively.
Future Trends in IAM
I believe new trends like GenAI, ML & AI research, and Blockchain will heavily impact IAM.
AI and Machine Learning: These technologies are increasingly used to enhance behavioral analytics, offering more nuanced and adaptive authentication mechanisms. Example: Okta’s Adaptive Multi-Factor Authentication (MFA) uses machine learning to assess the risk of each authentication request. It considers the user's location, device, network, and behavior to assign a risk score to each login attempt. If the risk score is high, it prompts for additional authentication factors. This dynamic approach ensures a balance between security and user convenience, adapting to the access risk level in real-time.
Decentralized Identity: Blockchain technology is paving the way for self-sovereign identities, potentially revolutionizing how identities are managed and controlled, moving away from centralized models. Example: Decentralized identifiers (DIDs) and attestations on the Ethereum blockchain allow for secure and private verification of credentials. This system enables entities to issue tamper-proof, cryptographically verifiable claims, which anyone can check against the issuer's DID on the blockchain. Such a mechanism is crucial for maintaining the integrity and privacy of personal and professional qualifications in a digital economy.
Ways to prepare: To position your security system for adaptability to future trends, ensure you Invest in Talent and Training, Adopt Agile and Scalable Architectures, Leverage Advanced Analytics, Implement Continuous Authentication and Authorization, Enhance Data Privacy and Security, etc.
Conclusion
The top IAM tools for 2024, including IBM Security Identity and Access Assurance, Microsoft Azure Active Directory, Ping Identity, Google Cloud IAM, and ManageEngine ADManager Plus, offer unique strengths to address the evolving security landscape. Cerbos’ unique strength is its policy-as-code approach, seamlessly integrating with these tools to enhance authorization capabilities. This synergy between authentication and authorization ensures robust security frameworks catering to diverse organizational needs. As we embrace future trends like AI and blockchain, these IAM tools, complemented by Cerbos, are poised to offer even more sophisticated, adaptable solutions to meet the challenges of digital identity management.
Get Signed Up for Cerbos Hub Today!
Cerbos has launched Cerbos Hub to provide a robust, dynamic, automated authorization management system. The Cerbos PDP ensures that authorization logic is transparent, version-controlled, and easy to manage. Cerbos Hub's managed service extends this power, seamlessly integrating with development workflows, providing real-time updates, and ensuring that authorization decisions are made efficiently everywhere, even at the edge.
Sign up to Cerbos Hub now and save months of developing access control in-house.
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team

