Broken Access Control is the #1 issue in OWASP 2021 Top 10
The Open Web Application Security Project (OWASP) is a nonprofit foundation that works to improve the security of software. Many will be familiar with the OWASP Top 10 which is published every few years and is used as the standard for evaluating the security of web applications.
The 2021 Top 10 has just been released and the top issue facing the industry is Broken Access Control. Having climbed from #5 in 2017.
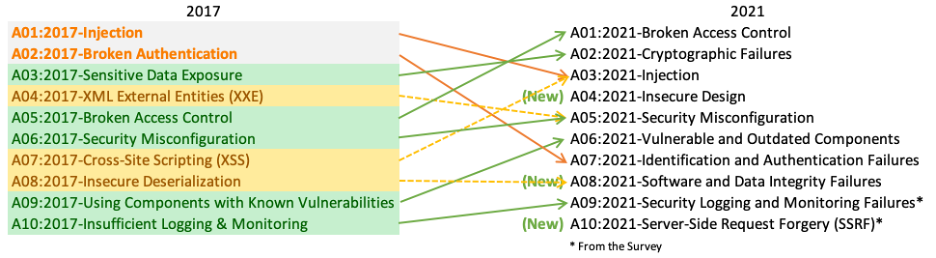
As a team we have worked in numerous businesses and had to ensure our products could stand up against the OWASP list when going through a pentest or compliance audit and access control was always an area of concern so we are not surprised to see it in the top spot.
Our mission with Cerbos is to ensure no one ever has to spend valuable time building access control and give the community a plug and play solution so that when it comes to the next audit or quarterly pentest it is no longer a concern.
Digging more into what OWASP has classed as “Broken Access Control” reveals all the areas that teams designing authorization need to consider - the majority of which Cerbos’ policies based ABAC controls can support:
Access control enforces policy such that users cannot act outside of their intended permissions. Failures typically lead to unauthorized information disclosure, modification, or destruction of all data or performing a business function outside the user's limits. Common access control vulnerabilities include:
-
Violation of the principle of least privilege or deny by default, where access should only be granted for particular capabilities, roles, or users, but is available to anyone.
-
Bypassing access control checks by modifying the URL (parameter tampering or force browsing), internal application state, or the HTML page, or by using an attack tool modifying API requests.
-
Permitting viewing or editing someone else's account, by providing its unique identifier (insecure direct object references)
-
Accessing API with missing access controls for POST, PUT and DELETE.
-
Elevation of privilege. Acting as a user without being logged in or acting as an admin when logged in as a user.
-
Metadata manipulation, such as replaying or tampering with a JSON Web Token (JWT) access control token, or a cookie or hidden field manipulated to elevate privileges or abusing JWT invalidation.
-
CORS misconfiguration allows API access from unauthorized/untrusted origins.
-
Force browsing to authenticated pages as an unauthenticated user or to privileged pages as a standard user.
You can read the full OWASP 2021 Top 10 here and if you want to learn more about how Cerbos can mitigate these issues in your application check out our documentation and join our Slack Community.
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
